Solution Background
With the acceleration of digital transformation, a logistics enterprise has become increasingly reliant on its information systems, making it more vulnerable to cybersecurity threats:
- Complex Threat Landscape: Internal vulnerabilities now pose greater risks than external attacks. Traditional security measures—such as firewalls and intrusion detection systems (IDS)—struggle to address modern threats like fileless attacks, zero-day exploits, and advanced persistent threats (APTs). Single-point security tools generate an overwhelming number of false or irrelevant alerts, often obscuring critical attack indicators.
- Inefficient Security Operations: Although the enterprise has deployed multiple security solutions, the lack of unified visibility across network, endpoint, and cloud environments hinders efficient threat analysis. Security teams are forced to manually investigate threats across disparate platforms, leading to delayed responses. This challenge is compounded by a shortage of skilled cybersecurity professionals, further straining operational efficiency.
- Tightening Industry Regulations: The growing frequency of data breaches and supply chain attacks has heightened the need for compliance with stringent data protection standards. To mitigate business risk, the organization must shift from passive defense to a proactive, integrated security approach.
Solution Summary
To address these challenges, the client restructured its security operations system using Cortex XDR, achieving end-to-end threat lifecycle management through the following capabilities:
- Intelligent Threat Detection and Blocking: Leveraging machine learning and behavioral analytics, Cortex XDR detects and blocks malware, exploit attempts, and fileless attacks in real time. It integrates global threat intelligence for adaptive, context-aware defense.
- Unified Alert Correlation: Multi-source alerts from network, endpoint, and cloud environments are automatically correlated into unified attack incidents. This eliminates data silos and presents a comprehensive view of the attack chain for faster investigation.
- Automated Root Cause Analysis and Response: AI-driven analysis pinpoints the root cause of incidents, automatically generates a timeline of attack activities, and enables one-click isolation of compromised endpoints or termination of malicious processes.
- Threat Hunting and Continuous Optimization: With native MITRE ATT&CK framework integration, Cortex XDR supports custom behavior-based rules and codifies threat-hunting expertise, enabling continuous optimization and expansion of threat detection coverage.
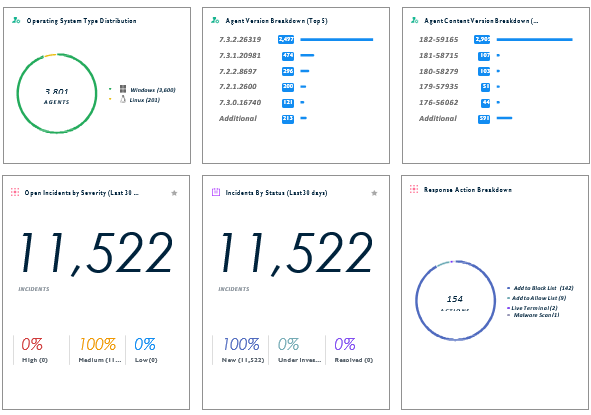
Key Advantages
- Detection Capabilities: Industry-leading detection of fileless attacks powered by AI-based behavioral models.
- Data Integration: Enables correlation analysis of Palo Alto native telemetry with third-party logs (e.g., firewalls, cloud platforms).
- Operational Efficiency: High alert compression rate, with average investigation time reduced to minutes—minimizing dependence on manual analysis.
- Scalability: Open APIs support integration with orchestration platforms, enabling cross-tool scripted responses and compatibility with multi-cloud or hybrid IT architectures.
Customer Pain Points & Challenges
- Outdated Defense Systems: Legacy security products are ineffective against advanced threats, leaving large detection blind spots.
- Alert Overload: Disconnected tools generate tens of thousands of alerts daily, with high false positives causing critical threats to be overlooked.
- Talent Bottlenecks: Analysts must switch between multiple consoles, wasting time on repetitive tasks. High staff turnover further weakens security operations.
- Lack of Visibility: No unified view across network, endpoint, and cloud; difficult to trace lateral movement and stealth threats.
Customer Benefits
- Improved Security Performance: Higher interception rate of unknown threats; significantly faster response to exploit-based attacks.
- Optimized Operational Costs: Less manual effort required for alert triage; shortened training cycles for new analysts.
- Enhanced Compliance: Automatically generates forensic reports that align with regulatory standards, increasing audit-readiness.
- Long-Term Value Retention: Embedded threat-hunting knowledge enables evolving detection rules, reducing repeat incidents year-over-year.