Solution Background
With the advancement of digital information technologies, educational institutions
are increasingly focusing on improving their capabilities in managing information
security incidents to prevent the malicious disclosure and misuse of faculty and
student data. The rise of AI has lowered the cost of cyberattacks while
simultaneously raising the bar for effective security defense.
By deploying Splunk, institutions can effectively address complex cybersecurity
threats, especially those targeting critical business systems and sensitive data.
The platform provides end-to-end visibility, advanced analytics, and automated
response capabilities, significantly enhancing the maturity of an organization's
security operations.
Solution Overview
- Data Integration and Processing Capabilities: Enables automated collection, processing, and analysis of logs from multiple data sources (e.g., network devices, endpoints, firewalls, cloud platforms), dramatically reducing manual intervention.
- Real-Time Event Processing and Response: Offers real-time monitoring and response to security events, ensuring that institutions can react quickly to complex and fast-evolving threats.
- Powerful Search and Analysis Engine: Features a robust search language that supports deep data mining and custom queries to help identify potential risks and abnormal behavior.
- Visualization and Reporting: Customizable dashboards and reporting tools tailored to the actual security posture of the organization, aiding management in timely decision-making.
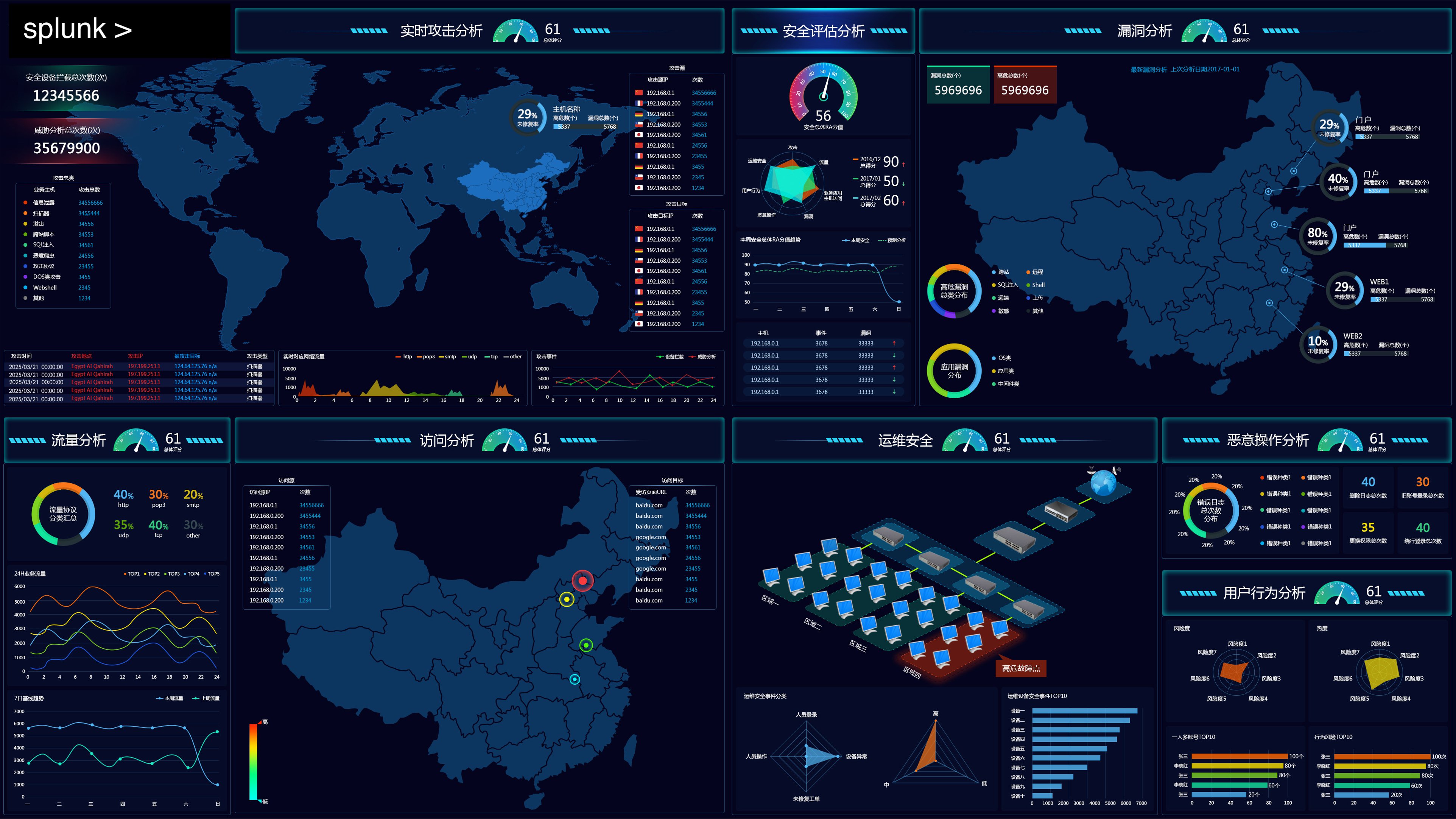
Key Features & Advantages
By utilizing Splunk, customers can solve the following challenges:
- Seamless integration and data fusion across multi-vendor products
- Efficient event management and investigation
- Real-time visibility into overall security posture, with automated threat detection and response
Customer Benefits
By deploying Splunk, customers gain:
- Comprehensive Security Visualization: Health monitoring of Exchange services (availability, attack attempts, abnormal login detection) Heatmaps showing sensitive data flow (by department, file type, or user) Integrated display of threat intelligence dynamics
- Improved Detection Efficiency: Average threat detection time reduced from hours to minutes. Higher recognition rate for vulnerability exploitation attempts. Increased accuracy in abnormal behavior detection
- Exchange Service Assurance: Significant improvement in email system availability and stability
Value Highlights
- Security Value: Builds a proactive defense framework that significantly reduces the risk of personnel data leakage.
- Business Value: Ensures stable operation of core education systems and supports the digital transformation of teaching.
- Management Value: Establishes a data-driven decision-making mechanism to enhance the organization's security maturity.
- Economic Value: Achieves return on investment (ROI) in the first year and continues to generate operational benefits.