Project Background
As the pace of digital transformation accelerates, the demand for remote access from
employees, partners, and customers continues to grow. At the same time, cyber
threats such as malware intrusions and data leakage are becoming increasingly
severe, posing significant risks to information security and business continuity.
To address these challenges, the enterprise decided to deploy an endpoint secure
access system to enforce strict identity verification and security assessments on
all network-connected devices. Only compliant devices are allowed to access
sensitive resources. After evaluating multiple solutions, the company selected a
secure access platform to build a unified and efficient network security
environment.
Solution Overview
The secure access authentication platform is an enterprise-grade security solution that integrates identity authentication, device management, and threat prevention. By deeply combining network access control with endpoint security management, the platform automates the entire process from user authentication to device health inspection. The enterprise deployed the following core components:
- Identity Authentication Server: Authenticates users attempting to access the network. Supports multiple authentication methods such as passwords, digital certificates, and two-factor authentication (2FA).
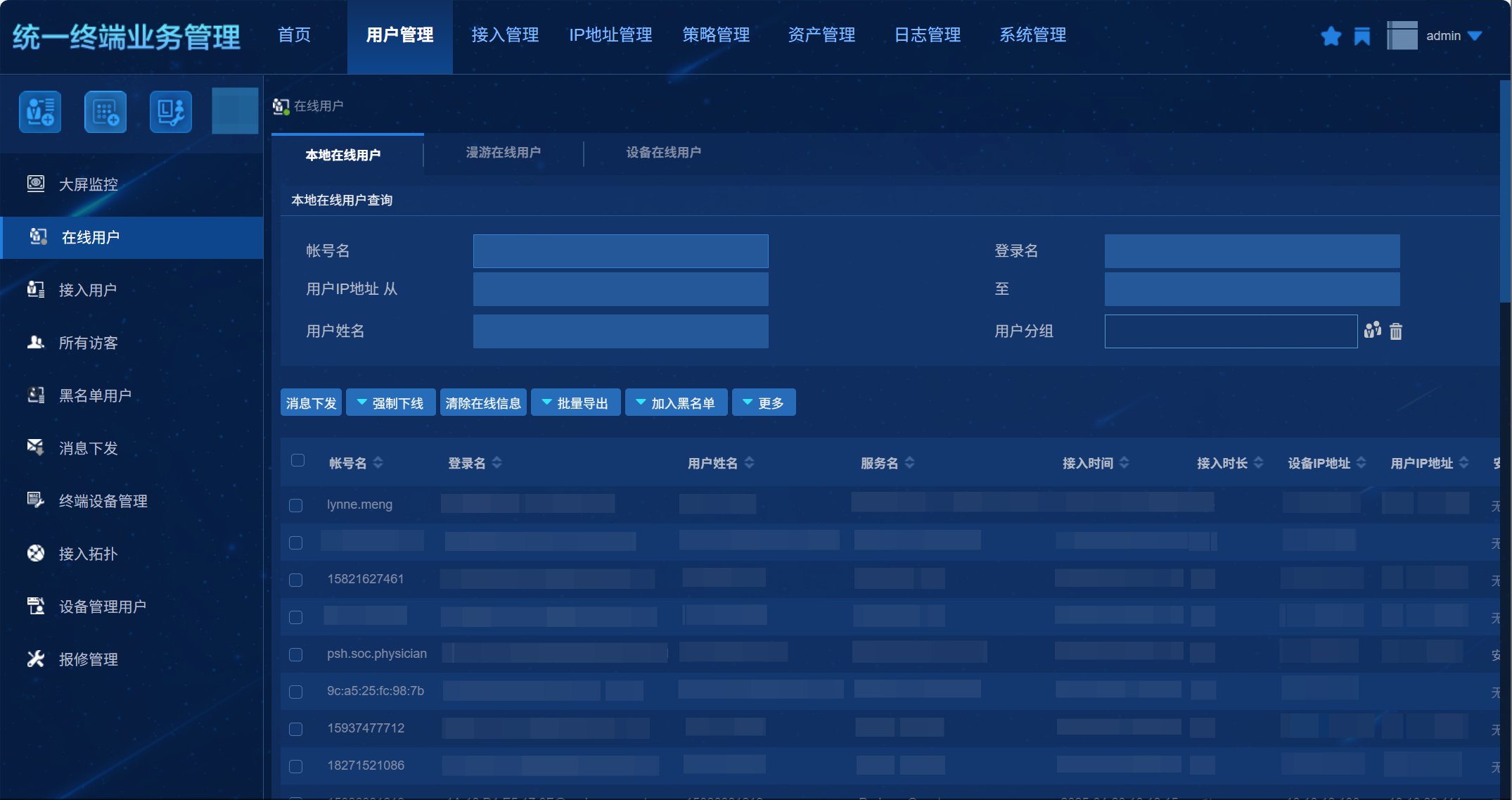
- Device Management System: Centrally manages all types of terminal devices including PCs, mobile phones, and IoT devices. Performs health checks and enforces security policies.
- Security Protection Module: Provides intrusion detection, antivirus, web filtering, and other protection functions to safeguard the network environment.
- Management Console Offers an intuitive user interface for administrators to configure and manage the entire system with ease.
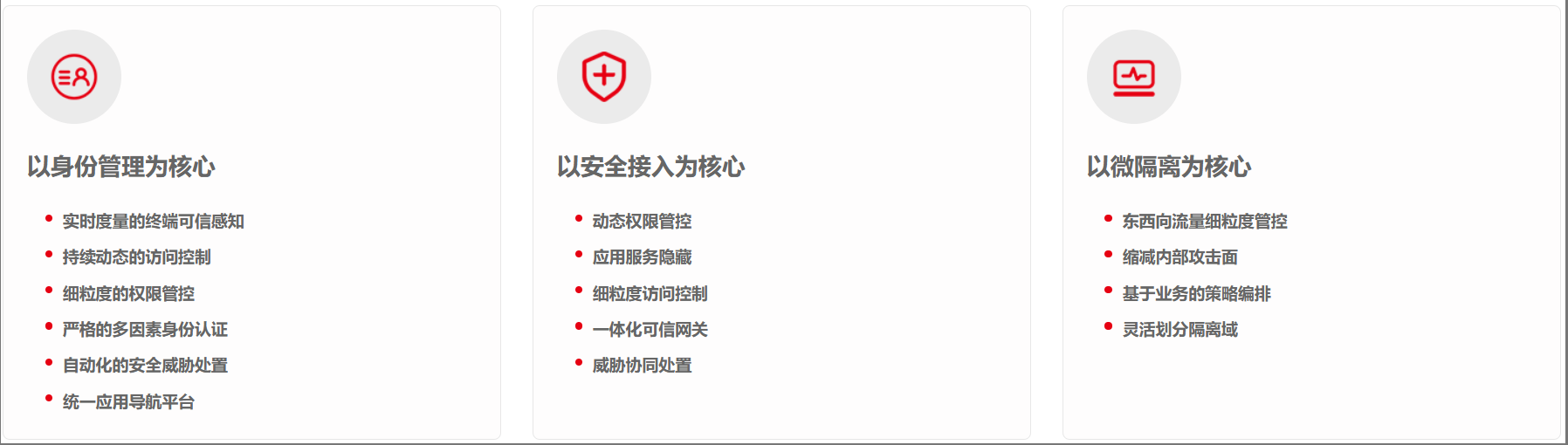
Key Features & Advantages
- Dynamic Access Control: Adjusts access permissions in real time based on user behavior, device status, and other risk indicators—enabling more flexible and precise security protection.
- Comprehensive Risk Assessment: Considers multiple dimensions including user behavior, device condition, and network environment for fine-grained risk evaluation and improved security.
- Principle of Least Privilege: Allocates only the minimum necessary access rights based on job requirements to reduce security risks caused by excessive permissions.
- Continuous Monitoring & Response: Continuously monitors user activity, and once abnormal behavior or potential threats are detected, access is immediately blocked and a response mechanism is triggered.
Customer Pain Points & Challenges
- Security Vulnerabilities: Without effective access control, the enterprise network is frequently exposed to external attacks and internal data leaks.
- Complex Network Management: As the organization expands, the increasing number and diversity of networked devices make traditional management approaches insufficient.
- Poor User Experience: Traditional access control solutions often require complex user-side configurations and operations, reducing user efficiency and satisfaction.
Customer Value
- Stronger Security Posture: Strict endpoint checks and identity authentication effectively block unauthorized devices and potential threats, reducing data breaches and malicious attacks.
- Improved Operational Efficiency: Centralized management and automation reduce manual efforts and streamline security processes. Dynamic permission assignment enhances flexibility and efficiency.
- Regulatory Compliance: Detailed audit logs and reporting functions help the enterprise meet industry regulations and internal policies, ensuring smooth external audits.
- Optimized User Experience: Despite enhanced security controls, user-friendly technologies like seamless authentication and guided issue resolution ensure legitimate users can access resources smoothly—boosting productivity and satisfaction.