Solution Background
In today's wave of digital and intelligent transformation, nearly all enterprises are undergoing changes. Business operations are increasingly internet-based and mobile-oriented. To ensure faster and safer deployment and iteration, enterprise application architectures and deployment models have undergone major transformations. The most commonly adopted application architectures face several challenges, such as resource waste, high expansion costs, significant processing latency, and weak threat resistance.
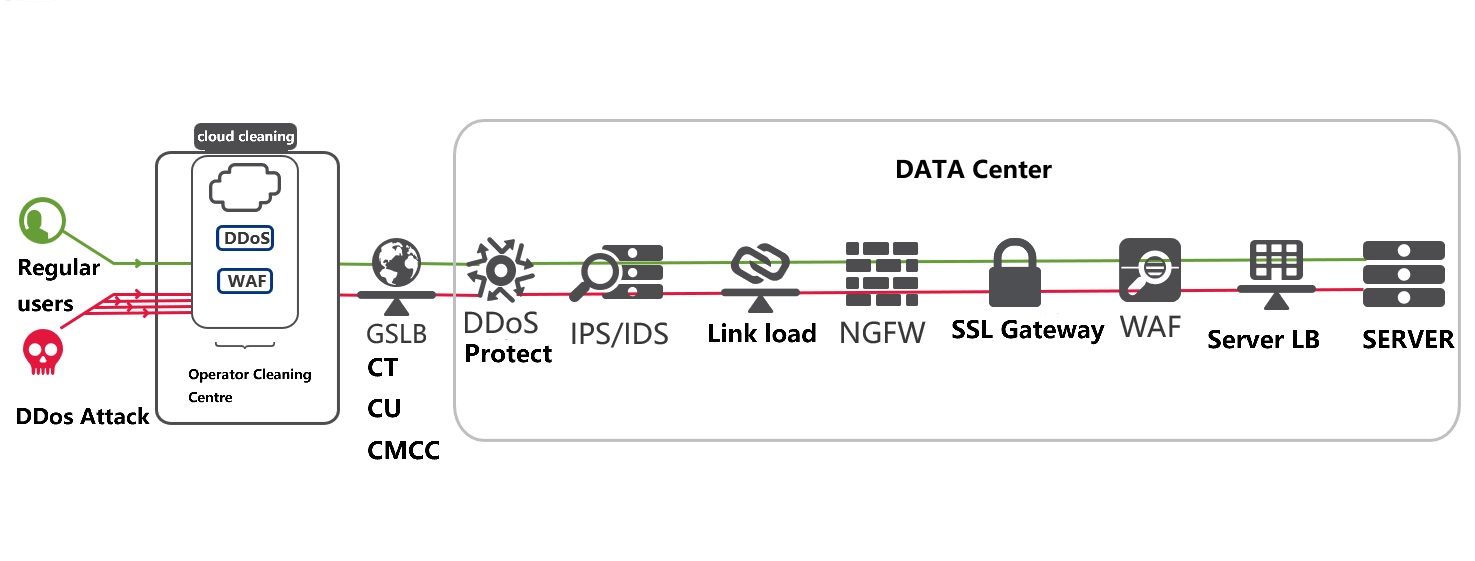
Solution Overview
- The SOC center pre-configures filtering policies for high-risk security events identified by the WAF and extracts critical information such as client IPs.
- Through automated scripts, the SOC center periodically pushes these client IPs to the firewall's blocking policies via API integration.
- The firewall then performs real-time blocking based on the security policy.
- Risk IPs are collected and blocked in real time without manual intervention, simplifying operational procedures and shortening the window for threat exploitation.
- Security events are aggregated to help clients discover potential vulnerabilities and implement proactive security strategies.
- SSLO virtualizes the WAF resource pool and supports integration with other security devices.
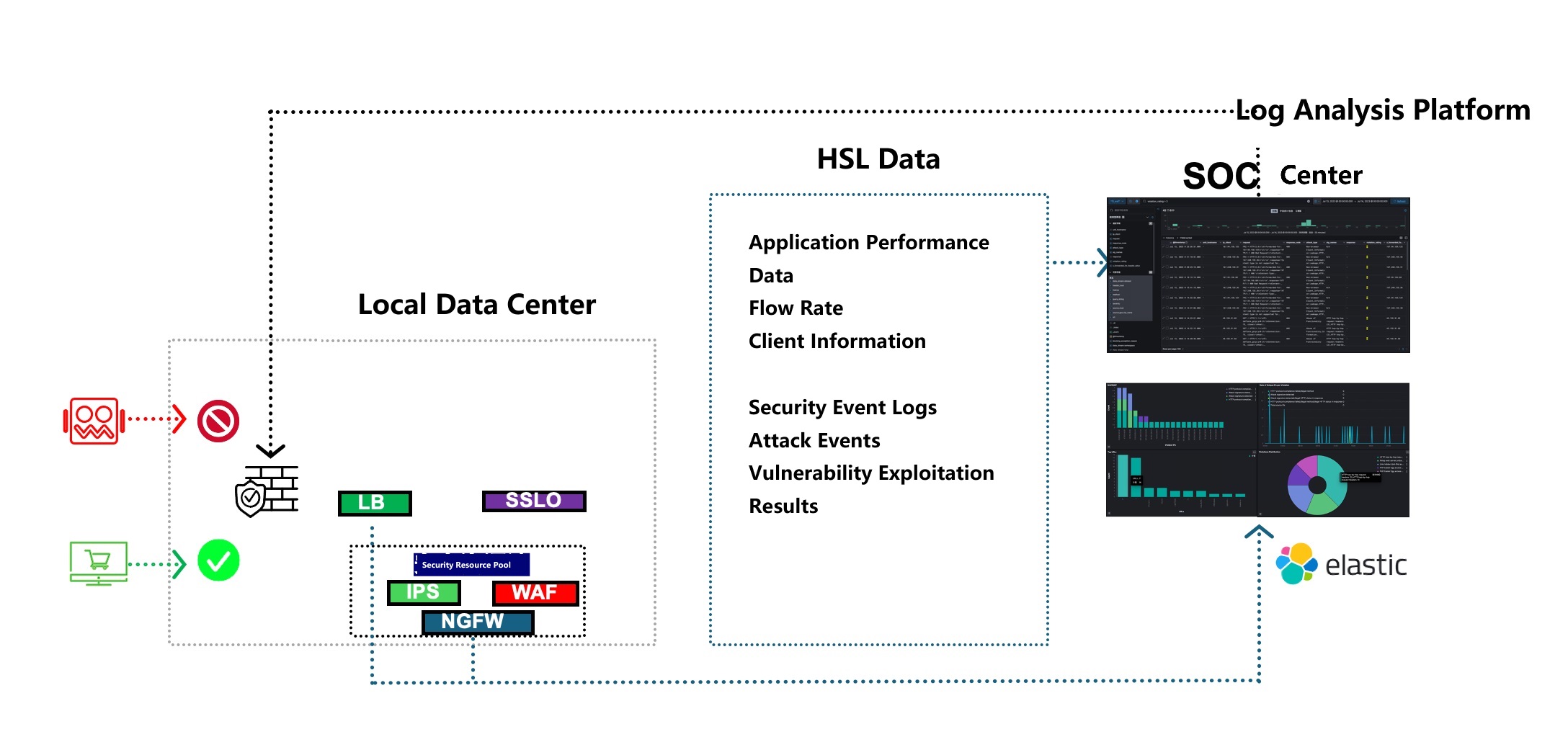
Key Advantages
- High Efficiency: Intelligent orchestration of inbound HTTP/HTTPS traffic, forwarding it to the WAF resource pool for inspection.
- Resource Saving: Flat resource pool structure improves flexibility and utilization in operations.
- Effective Blocking: Log analysis platform extracts suspicious client IPs based on WAF logs and pushes them to the firewall for real-time blocking.
- Traceability: Enables log queries based on exploitation details to trace event time and method, helping assess potential service degradation or outages.
- Scalability: SSLO supports flexible traffic orchestration to meet future expansion and heterogeneous integration scenarios.
Customer Challenges
This application-layer security solution addresses the following key challenges for customers:
- Overly complex security architecture design
- Ever-present risk of security incidents
- Lack of visibility into both business and security events
Customer Benefits
By adopting this security protection solution, customers gain the following benefits:
- Security Resource Pooling & Elastic Expansion: Loosely coupled security devices allow flexible scaling.
- Centralized SSL Handling: Reduces performance load on security devices during SSL encryption/decryption and ensures data security.
- Intelligent Traffic Orchestration: Enables on-demand use of resources, improving utilization and reducing latency.
- Deep Health Checks with Agile Failover: Enables quick bypassing of failure points to maintain business continuity.
- Pluggable Security Capabilities: Security devices can be easily added or removed, enhancing architectural flexibility and reducing O&M costs.
- Automated Security Protection: Lowers protection costs by automatically stopping ongoing attacks and breaking the attack chain.